Finding IT Solutions: Managed Service Providers Near Me Introduced
Finding IT Solutions: Managed Service Providers Near Me Introduced
Blog Article
Strategize and Range WITh Proven IT Managed Services Strategies
In the busy landscape of contemporary service, the calculated usage of IT handled services has come to be a cornerstone for organizations intending to enhance functional performance and drive lasting growth. By carrying out tested methods tailored to fulfill certain organization needs, business can browse the intricacies of technology while staying affordable and nimble in their particular sectors.
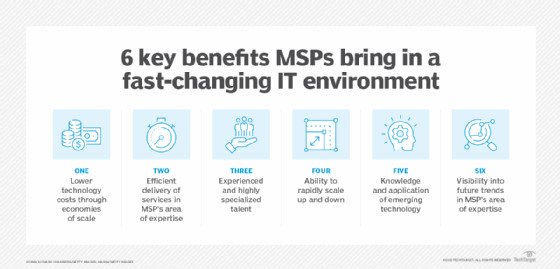
Advantages of IT Handled Services
By outsourcing IT administration to a specialized service provider, companies can touch into a wealth of knowledge and resources that would otherwise be costly to maintain internal. One of the vital advantages of IT Handled Provider is aggressive tracking and upkeep of systems, which assists avoid prospective concerns before they rise right into significant issues.
Moreover, IT Took care of Solutions can supply access to the most recent modern technologies and best practices without the requirement for constant investment in training and framework upgrades. This ensures that businesses remain competitive in a quickly advancing technological landscape. Additionally, by unloading routine IT tasks to a taken care of companies, interior IT teams can concentrate on strategic initiatives that drive technology and growth for the organization. To conclude, the advantages of IT Managed Services contribute in simplifying operations, improving effectiveness, and eventually, driving business success.
Trick Approaches for Implementation
With an understanding of the substantial advantages that IT Took care of Solutions deal, organizations can currently focus on carrying out key methods to effectively incorporate these solutions right into their procedures - msp association of america. In addition, companies must establish clear communication networks with their handled solution copyright to make certain seamless partnership and timely issue resolution.
Another critical strategy is to prioritize cybersecurity steps. Information breaches and cyber hazards pose considerable threats to businesses, making safety and security a top priority. Executing durable security methods, routine monitoring, and prompt updates are necessary action in protecting delicate info and preserving organization connection.
Furthermore, organizations should develop solution degree contracts (SLAs) with their handled company to specify expectations, responsibilities, and efficiency metrics. SLAs aid in establishing clear standards, guaranteeing accountability, and preserving service top quality requirements. By including these essential strategies, services can leverage IT Handled Services to simplify procedures, enhance efficiency, and drive sustainable growth.
Making Best Use Of Performance Via Automation

In addition, automation allows real-time surveillance and information analysis, supplying useful understandings for notified decision-making. By automating regular monitoring tasks, organizations can proactively resolve concerns prior to they escalate, minimizing downtime and maximizing efficiency (managed service providers). In addition, automation can facilitate the smooth assimilation of various systems and applications, improving partnership and data flow throughout the company
Ensuring Data Safety and Compliance
Data security and compliance are paramount problems for companies operating in the digital landscape of today. With the raising go to website volume of sensitive information being saved and processed, making sure robust safety procedures is critical to secure against cyber threats and abide by regulative demands. Carrying out detailed data safety and security practices entails securing information, establishing gain access to controls, consistently upgrading software application, and conducting safety and security audits. Conforming with laws such as GDPR, HIPAA, or PCI DSS is vital to keep and avoid costly charges count on with customers. Handled IT services suppliers play a crucial role in aiding More Info companies navigate the complex landscape of information security and compliance. They use know-how in carrying out safety and security protocols, keeping track of systems for possible breaches, and ensuring adherence to market policies. By partnering with a trustworthy took care of providers, businesses can boost their information security pose, alleviate risks, and show a dedication to shielding the privacy and integrity of their information assets.
Scaling IT Facilities for Development
Incorporating scalable IT infrastructure options is essential for assisting in service growth and functional effectiveness. As companies increase, their IT needs progress, needing facilities that can adjust to increased demands flawlessly. By scaling IT facilities successfully, organizations can make certain that their systems remain reputable, safe, and performant even as work grow.
One trick facet of scaling IT infrastructure for development is the ability to flexibly designate resources based on current demands. Cloud computing solutions, for instance, deal scalability by enabling businesses to readjust storage space, processing power, and other resources as needed. This elasticity enables companies to effectively manage spikes sought after without over-provisioning sources throughout periods of reduced task.
Moreover, carrying out virtualization modern technologies can improve scalability by enabling the creation of virtual circumstances that can be quickly duplicated or changed to suit altering workloads - Managed Service Providers near me. By virtualizing web servers, storage space, and networks, companies can optimize source application and simplify IT management processes, eventually supporting service development efforts efficiently
Final Thought
In verdict, applying IT took care of solutions can bring numerous advantages to an organization, such as boosted read this performance, boosted information protection, and scalability for development. By following key methods for application, using automation to make the most of performance, and ensuring data security and conformity, businesses can much better strategize and scale their IT facilities. It is critical for organizations to develop and adapt with technological developments to stay competitive in today's ever-changing landscape.
Report this page